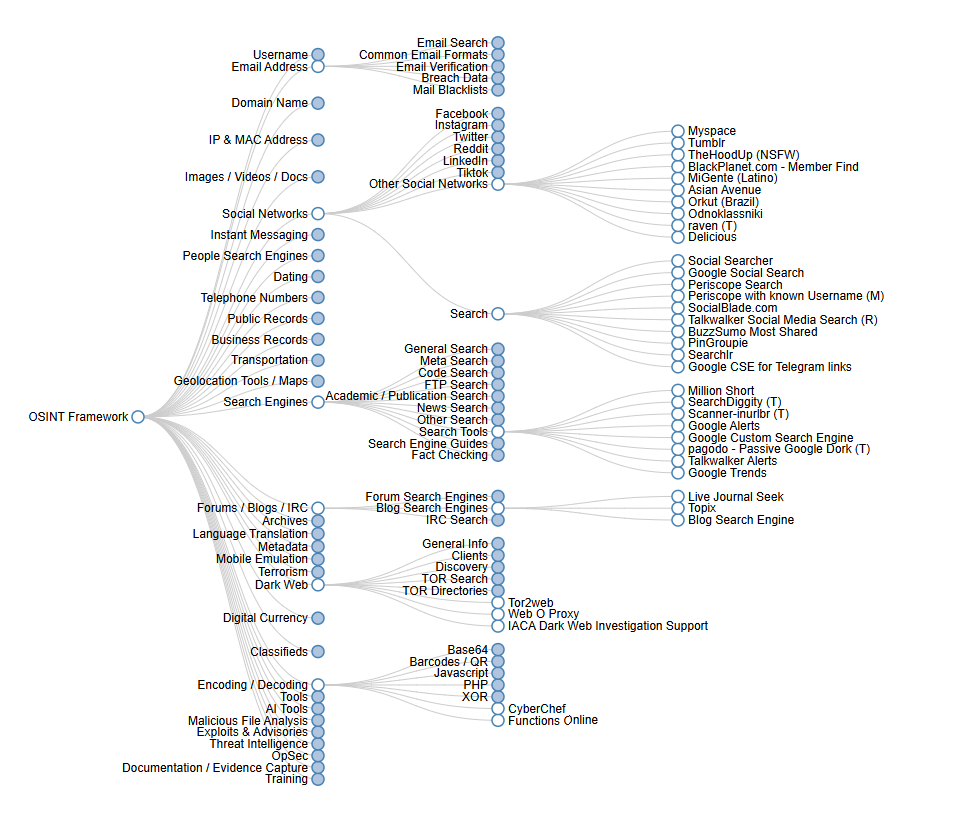
In today’s interconnected world, Open Source Intelligence (OSINT) has become an essential methodology for collecting and analyzing publicly available information to produce actionable intelligence. Originally developed for military intelligence purposes, OSINT has evolved into a powerful tool used across various sectors, from cybersecurity to business intelligence. According to Wikipedia’s definition, OSINT refers to data collected from publicly available sources to be used in an intelligence context. This systematic approach to information gathering has transformed how organizations and individuals understand and interact with publicly available data.
The evolution of OSINT
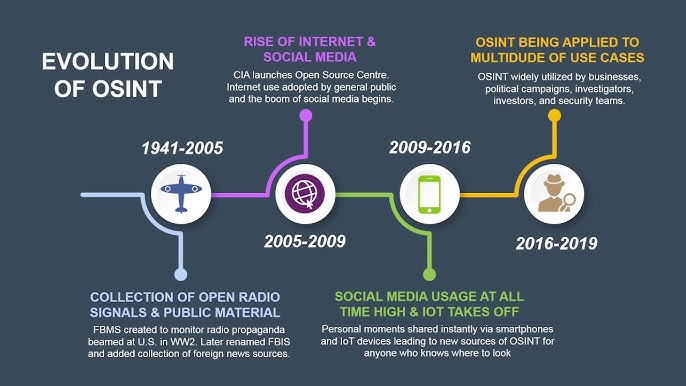
The concept of open-source intelligence has transformed dramatically since its inception during World War II. Initially focused on traditional media and public documents, OSINT has evolved into a sophisticated discipline encompassing vast digital landscapes. Today’s OSINT practitioners navigate an ocean of information spanning social media, academic databases, corporate records, and countless other digital sources.
Information sources in the OSINT ecosystem
The contemporary OSINT environment draws from a diverse range of sources:
-
Traditional Media: Newspapers, broadcast networks, and other established media outlets continue to provide valuable information.
-
Digital Media and Social Networks: Platforms such as Twitter, Facebook, LinkedIn, and Instagram offer real-time insights into public sentiment, behavioral patterns, and emerging trends.
-
Professional and Academic Resources: Scientific publications, research papers, and industry reports deliver in-depth analyses across various fields.
The OSINT intelligence Cycle
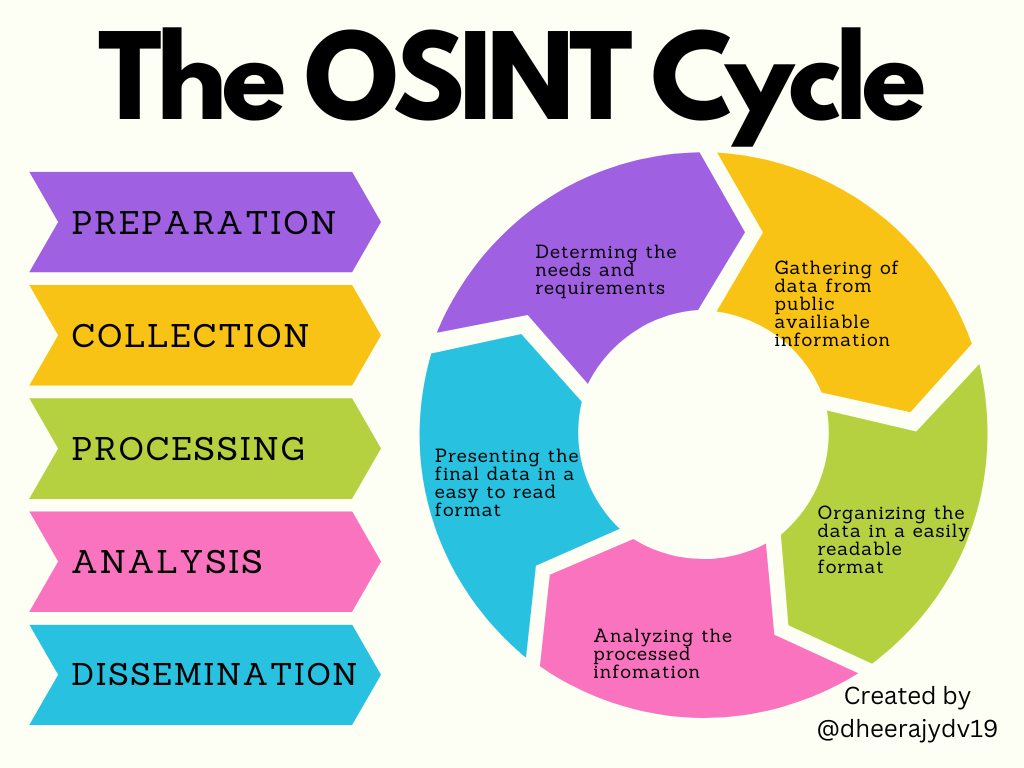
The OSINT Cycle, designed by Dheeraj Yadav
The process of OSINT can be delineated into several key phases:
-
Planning and Direction: Establishing clear objectives, identifying relevant sources, and setting analysis parameters.
-
Collection and Processing: Systematic gathering of information using tools ranging from advanced search engines to specialized data extraction methods.
-
Analysis and Production: Transforming raw data into actionable intelligence by identifying patterns, establishing connections, and drawing meaningful conclusions.
-
Dissemination and Integration: Sharing the produced intelligence with relevant stakeholders and integrating feedback to refine future OSINT activities.
Advancements in OSINT tools and techniques
The evolution of technology has significantly enhanced OSINT capabilities:
-
Automated Data Collection: Tools now enable the scanning of public networks and deep web content, uncovering data not indexed by traditional search engines.
-
Artificial Intelligence and Machine Learning: AI/ML technologies assist in analyzing vast datasets, identifying trends, and predicting potential threats, thereby augmenting human analytical capabilities.
Applications of OSINT
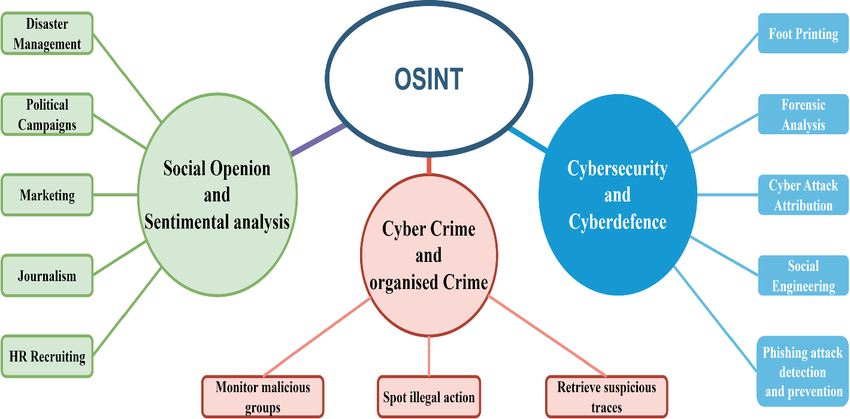
The practice of Open Source Intelligence (OSINT) has revolutionized how we gather and analyze publicly available information. Unlike traditional intelligence methods that rely on classified sources, OSINT harnesses the power of accessible data to generate valuable insights across multiple sectors.
In law enforcement and security, OSINT has become a game-changer. Investigators now routinely monitor social media, analyze public records, and track digital footprints to solve cases and prevent threats. This approach has proven particularly effective in cybercrime investigations, where digital breadcrumbs often lead to crucial breakthroughs.
Corporate applications of OSINT have transformed business intelligence. Companies leverage public data to assess market conditions, track competitors, and identify emerging opportunities. From analyzing consumer sentiment on social media to monitoring industry trends through public financial reports, OSINT provides businesses with a comprehensive view of their operational landscape.
Cybersecurity professionals rely heavily on OSINT techniques to protect digital assets. By monitoring threat intelligence feeds, analyzing vulnerability disclosures, and tracking malicious activities across the open web, security teams can proactively defend against emerging threats. This proactive approach has become essential in an era where cyber threats evolve rapidly.
Journalists and researchers have also embraced OSINT methodologies to enhance their investigations. Through careful analysis of public documents, social media activity, and online databases, they can verify facts, uncover connections, and build compelling narratives based on solid evidence.
As technology evolves, OSINT continues to gain importance. Advanced tools and techniques make it possible to process vast amounts of public data efficiently, while maintaining ethical standards and respecting privacy concerns. This balance between accessibility and responsibility remains crucial to the future of open source intelligence.
Legal and ethical considerations
While OSINT involves collecting publicly available information, practitioners must remain cognizant of legal and ethical boundaries, ensuring compliance with data protection regulations and respecting individual privacy rights.
In summary, OSINT has evolved into a sophisticated discipline integral to various fields, driven by technological advancements and the proliferation of digital information sources.
How OSINT is used by security teams and threat actors
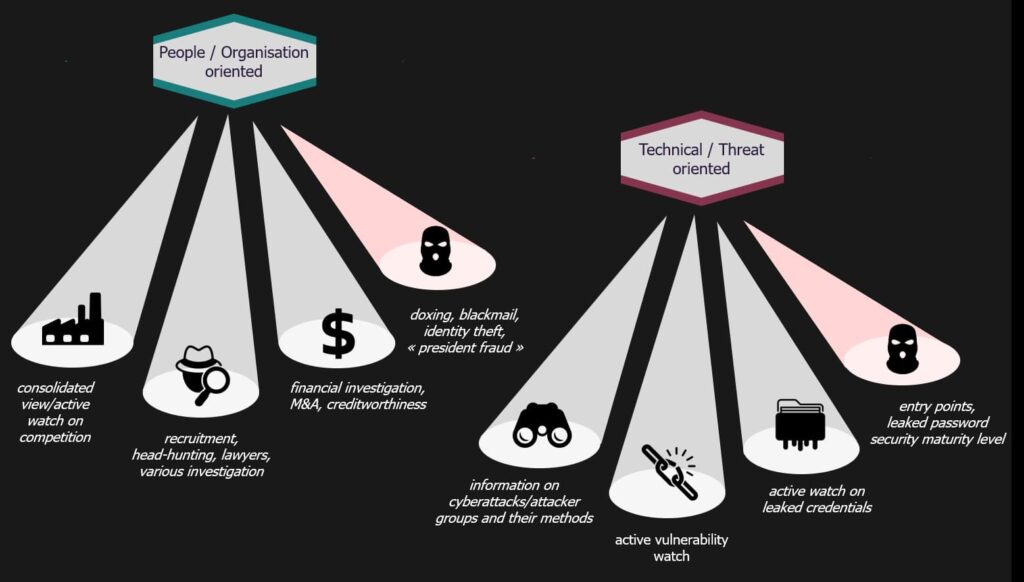
Open-source intelligence (OSINT) serves both defenders and attackers, playing a pivotal role in cybersecurity. Security teams use OSINT to uncover vulnerabilities, while malicious actors exploit it for targeted attacks and phishing schemes. Additionally, OSINT is employed to influence and monitor public opinion.
Defensive use of OSINT by security teams
For cybersecurity teams and penetration testers, OSINT is a critical tool for identifying publicly accessible information about an organization’s internal systems. This may include metadata inadvertently published online, revealing sensitive details such as open ports, unpatched software vulnerabilities, device configurations, and even leaked credentials. Social media platforms often serve as rich sources of such data, providing insights into employees, organizational structures, and IT environments. Even partnerships, vendor relationships, and acquisitions can inadvertently expose sensitive information.
By analyzing these public data points, security teams can mitigate risks, patch vulnerabilities, and secure exposed assets before attackers exploit them.
Offensive use of OSINT by attackers
Cybercriminals leverage OSINT to gather personal and professional details about employees, often via social media platforms. LinkedIn is particularly valuable, as it reveals job titles and organizational hierarchies, enabling attackers to craft convincing spear-phishing campaigns. Other social platforms can expose personal details such as birthdays, family names, and even pet names—information often used in password guessing or social engineering attacks.
Attackers also use OSINT to scan public networks for unpatched systems, misconfigured cloud resources, or exposed databases. Platforms like GitHub can inadvertently reveal sensitive information, as developers may embed credentials, passwords, or encryption keys in their code. Specialized tools allow attackers to efficiently locate and exploit these vulnerabilities.